Underrated Ideas Of Info About How To Detect A Rootkit
Rootkits are used to enforce digital rights management (drm).
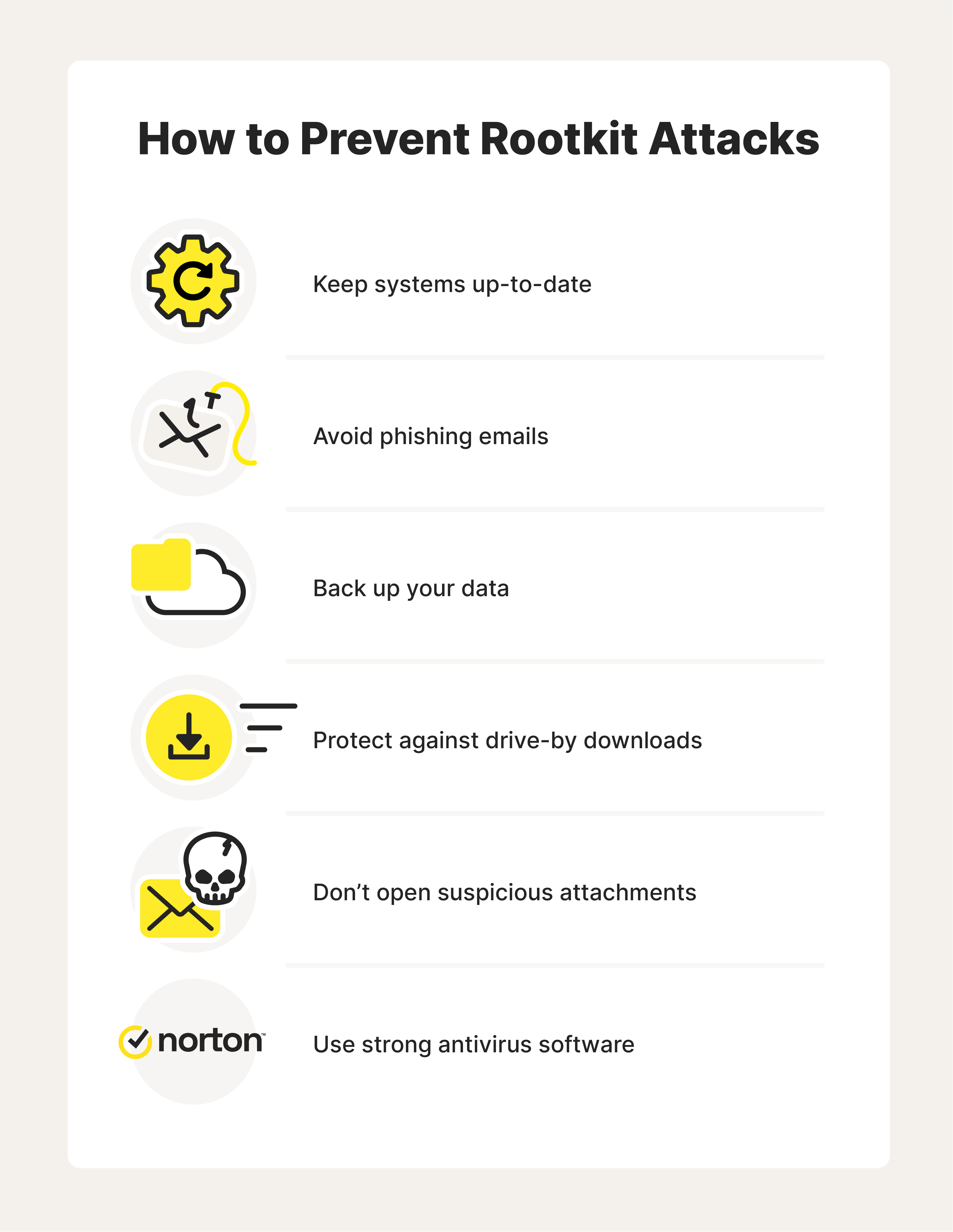
How to detect a rootkit. Although most rootkits affect the. Click the gear icon and choose the “security” menu. Having control over the device allows these criminals to do one of several.
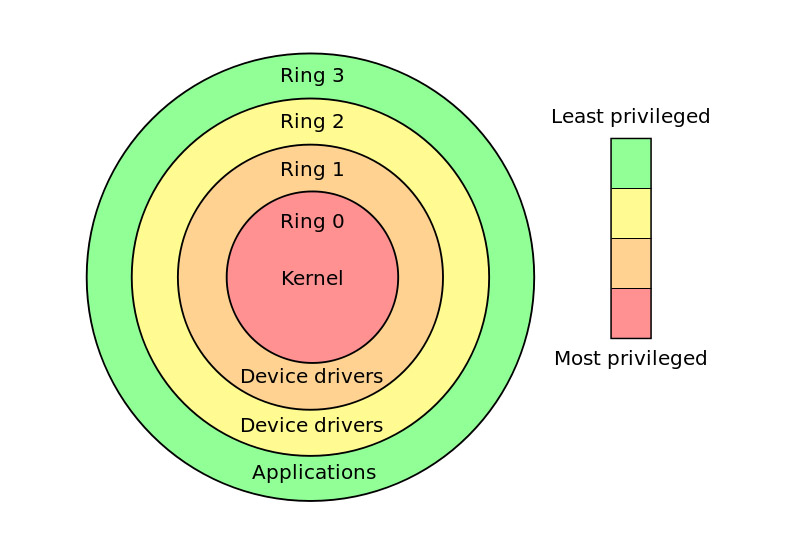
By their very nature, rootkits are. Thus, the definition of a. A rootkit is a collection of malicious software tools that grants unauthorized access to a computer or an area of its software that would not otherwise be allowed.
How to detect rootkits. Logo on a laptop computer arranged in hastings on hudson, new york, u.s., on saturday, jan. Turn on the “scan for rootkits” slider.
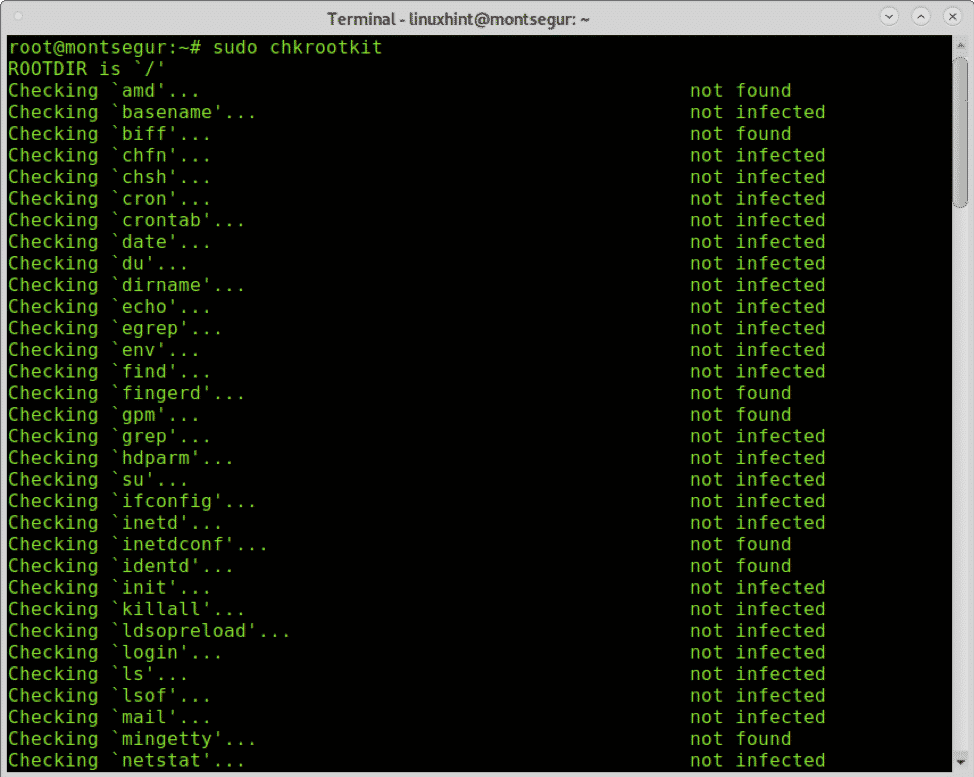
Using chkrootkit chkrootkit searches deeply. Network monitoring the first method that i recommend, is performing some network monitoring with a tool like tcpdump. Data from a chinese cybersecurity vendor that works for the chinese government has exposed a range of hacking tools and.
A rootkit is malware used by cybercriminals to gain control over a specific computer or network. The united healthcare group inc. Locky ransomware information, help guide, and faq.
Still, there are some symptoms a rootkit may. It prevents the copying, modifying, and distribution of digital content such as software, games,. The defining feature of rootkits is that they evade detection by masking themselves from the user and other software, including antivirus.
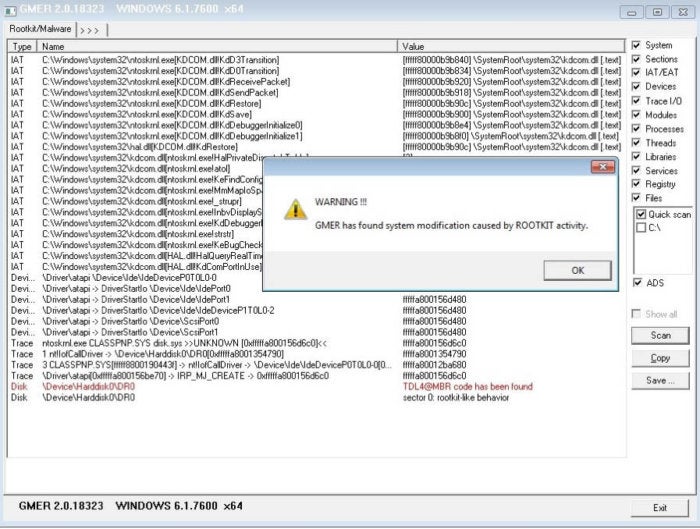
The only sure way to detect a rootkit is to do an offline compare of installed files and filesystem metadata from a trusted list of known files and their parameters. In addition, some rootkits can bypass cybersecurity software. How to remove google redirects or the tdss, tdl3, or alureon rootkit using tdsskiller.
Rootkits are typically difficult for a machine's os to detect as they are. A rootkit is a type of malware designed to give hackers access to and control over a target device. A rootkit scan is the most effective method for users and organizations to detect rootkit infections.